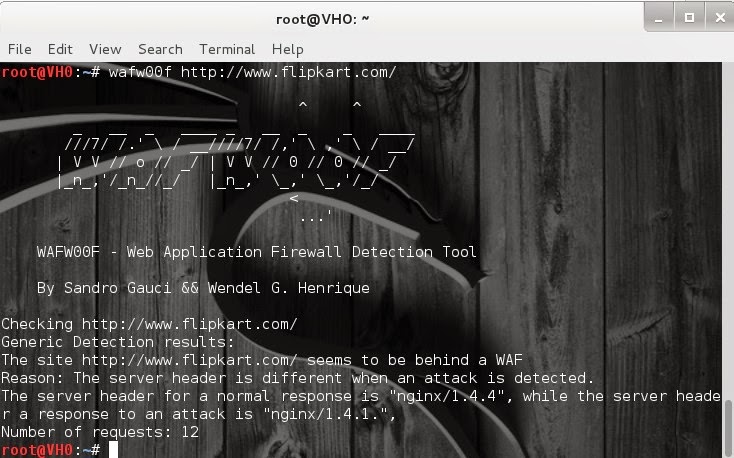
It’s one of the simplest but also most essential steps to
“Conquering” a network. Once a hacker has performed a “Man In The Middle”
attack (MITM) on a local network, he is able to perform a number of other
“Side-kick” attacks. This includes, cutting a victim’s internet connection;
intercepting Emails, logins, and chat messages; and many others.
And only one tools is needed for this attack:
An install or Live boot of Kali Linux, a well-known OS containing
a collection of hundreds of penetration testing tools.
If you have that, then proceed to the tutorial below, and we’ll
demonstrate how to perform this powerful attack.